Whenever you are logging in to an application, you might come across an option, namely “log in with Facebook.” Whether you are using Spotify or Pinterest, you know the drill! Being a user, you really don’t know how SSO Strategy OAuth works. All you want is to use the app and enjoy a smoother experience. Moreover, you want to remember fewer logins and passwords.
It is always imperative for a developer to work on an SSO Strategy to help provide users with a single sign-on experience. We at Webdecorum would love to offer you some ideas based on this subject.
For so many years now, there has been an attempt to achieve SSO, but the main focus needs to be on the difference between OAuth2 and SAML SSO.
The perfect need for SSO:
Nowadays, a platform houses multiple client applications; some of them are web-based, and others are native-like mobile apps. This platform needs to roll out to be easily accessible to different cities. Then you have the third-party apps that are to be crafted around this said platform.
The platform remains to a front-end subject to a large enterprise system with existing identity information about people who will use the same. Instead of having every client app maintains its own user database, it is better to utilize the power of SSO.
Single sign-on will allow the enterprise to store and own all user credentials securely. The platform will create a trusting relationship with the enterprise authentication server, and client apps can be crafted to use the trusted auth server to authenticate the users.
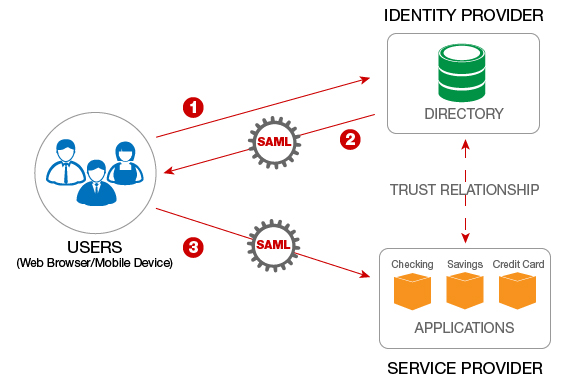
The value of SAML 2.0:
Previously, SAML authentication 2.0 was targeted to be a set of open standards, which was mainly designed for SSO. But the SAML 2.0 provides a web browser-based SSO strategy profile, talking about ways to use single sign-on for web apps. There are primarily three players related to SAML, and those are:
- Service Provider: From this web server, you can try to access information.
- Client: Here, the user knows how to interact with the resource server.
- Identity Provider: This server owns user identities and the credits. It is who the user mainly authenticates with.
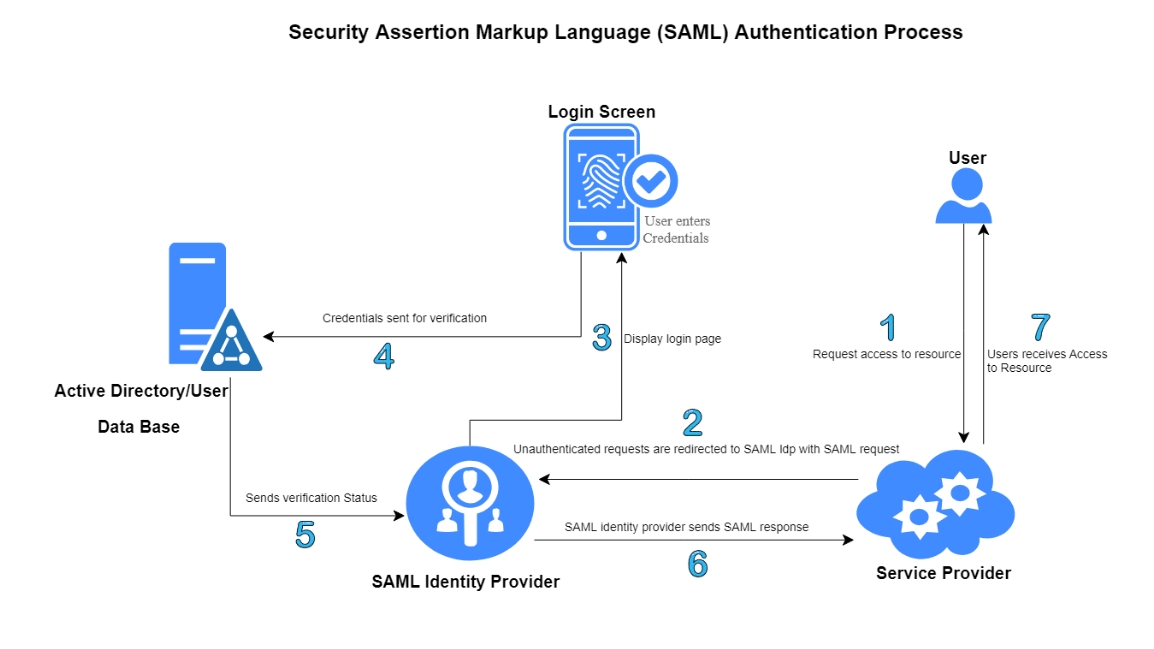
SAML token versus the SAML Assertion:
When people were first introduced to SAML, “SAML token” came up all the time. It is not a term in SAML spec, but people kept on using the same. Later, it was stated that SAML Token is a colloquial way to refer to “SAML Assertion.” It is mainly an XML node with some elements to it.
Now with OAuth 2.0:
Once you are sure of the SAML sector, it is time to focus on OAuth 2 implementation, particularly OAuth 2.0 in question. Unlike the SAML category, OAuth 2.0 is a specification whose link is still there. It has the power of being recent and has worked with the changing world in the past 8 years.
Right now, the native applications and mobile devices are working in such a way that SAML could not anticipate in 2005! The basic players with OAuth 2.0 are:
- Service provider: This is one web server that you are trying to gain information from.
- Client: This is a way in which the user interacts with Resource Server. It can be a browser-based web app, desktop all, server-side app, or even a native mobile app.
- Identity provider: This server owns the credits and user identities.
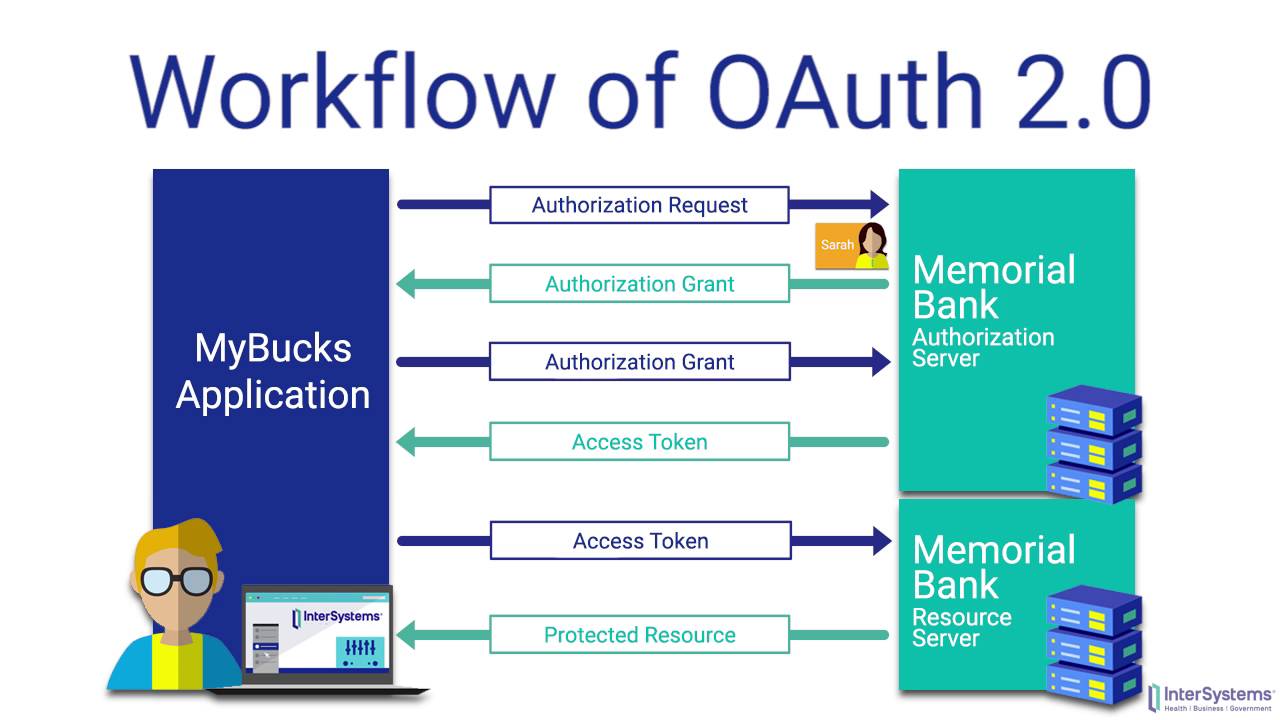
The OAuth authentication comes with the authorization code flow. OAuth 2.0 is known to offer three other flows that work a bit differently under multiple scenarios. For example, you have single-page JS apps, native desktop apps, native mobile apps, and traditional web apps where a user is not involved directly, but they have granted you the permission to do someone on their behalf.
The main advantage of the OAuth 2.0 flow is the communication from the Authorization Server back to the client and the Resource Server. It is done over HTTP Redirects with token information as mentioned to be query parameters. OAuth 2.0 won’t assume the client to be a web browser much like SAML.
The final verdict:
Before you proceed further with SSO single sign on, it is vital to learn about SAML and OAuth 2.0, and that’s when we at Webdecorum come to the rescue with some great ideas.
Overall, it can be stated that SAML has one major feature that OAuth 2.0 lacks. SAML token comprises user identity information mail because of the signing. With OAuth 2.0, you won’t get this value. Instead, the Resource Server will need to make an added round trip for validating tokens with the Authorization Server.
Then you have OAuth 2.0, which helps you to invalidate the access token on the Authorization Server. Later, it will disable it from any further access to Resource Server.
So, both platforms have features and cons to work for SSO strategy. Understanding the concept is vital before making the right choice, and that’s when Webdecorum comes to the rescue!
For more information and free consultation, please contact us at info@webdecorum.com or by click here.




